Executives expect their CISOs to translate complex cybersecurity challenges into clear business insights. In practice, this often means showing not just where risks exist but also how well programs are performing and whether investments are delivering value. Without a clear and consistent way to present this information, even strong cybersecurity programs can lose credibility with leadership, which reduces support for critical initiatives and increases the organization’s exposure to risk.
A well-designed CISO dashboard changes that dynamic. More than a reporting tool, it’s a strategic communication asset that consolidates critical security metrics and presents them through a business lens. This viewpoint allows CISOs to show how security investments contribute directly to business outcomes.
In a recent study, 64% of executive boards said that presenting cybersecurity as a business enabler was the most effective way to increase their budget. A CISO dashboard enables simplified tracking and communication of the KPIs that demonstrate business value, making it easier to secure the resources needed to strengthen defenses and meet compliance obligations.
For mid-market companies balancing compliance mandates, risk exposure, and limited resources, a CISO dashboard provides essential visibility into cybersecurity initiatives. Let’s break down what a CISO dashboard is, what it should include, and review nine actionable tips to build an excellent dashboard for your organization.
What is a CISO Dashboard?
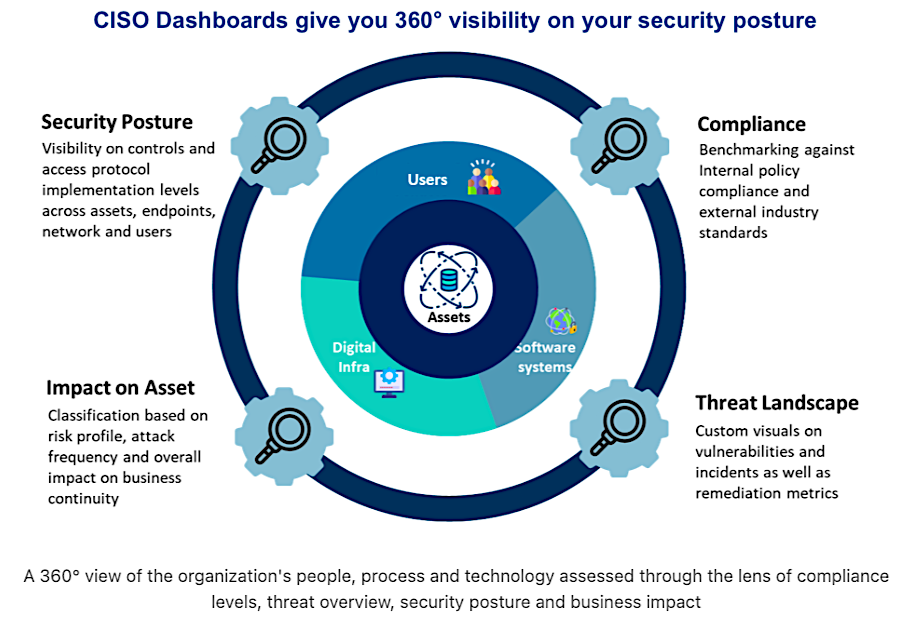
A CISO dashboard is a centralized software tool that brings together cybersecurity data and presents it in a way that leadership teams can use to make informed decisions. It collects inputs from security monitoring, compliance platforms, and IT operations, then translates that information into a 360-degree, executive-level view of risk, performance, and readiness.
CISOs and other security leaders, such as virtual CISOs, use these dashboards to track how their programs are performing, but the actual value lies in what the audience takes away from them:
- Executives and boards see a clear picture of organizational risk and whether investments are reducing exposure.
- Compliance officers gain visibility into gaps against frameworks such as NIST 800-171, CMMC, ISO 27001, and SOC 2.
- Operational teams can validate remediation progress and identify trends that need attention.
CISO dashboards are crucial for showing how well your organization’s cybersecurity program aligns with business priorities. It creates a shared language between technical leaders and non-technical stakeholders to ensure that decisions about funding, compliance, and strategy are based on accurate information.
Why You Need a CISO Dashboard
The pressure on CISOs and security leaders has never been higher. Regulatory requirements continue to expand across industries, from DFARS and CMMC for defense contractors to HIPAA in healthcare and PCI DSS in financial services. At the same time, boards and executive teams are asking for clearer visibility into risk and compliance. Without a structured way to present this information, security leaders risk being seen as cost centers rather than business enablers.
A CISO dashboard directly addresses these challenges by giving leaders the ability to:
- Demonstrate how security investments reduce organizational risk and support compliance obligations.
- Show progress over time on incident response, vulnerability management, and awareness initiatives.
- Justify budget and staffing needs by linking security performance to business outcomes.
- Assure customers, partners, and regulators during vendor due diligence or audit readiness reviews.
For mid-market firms that often operate with lean IT resources, a CISO dashboard becomes a critical mechanism to prove maturity, secure funding, and build trust with leadership.
6 Key Elements of an Effective CISO Dashboard
To turn your CISO dashboard into a decision-making tool, these six elements are essential:
1. Audience-specific Views
A dashboard must present information at the right level of detail for its consumers. Executives and boards require high-level summaries tied to business outcomes, while technical teams benefit from operational detail on vulnerabilities, incidents, and remediation status.
2. Visual Clarity
The design should highlight trends and status with simple formats such as scorecards, traffic-light indicators (RAG status), or trendlines. A clean presentation ensures that key findings can be absorbed quickly in executive meetings or audit reviews.
3. Logical Structure
Metrics should be grouped into meaningful categories, such as risk, compliance, and incident response. This setup avoids clutter and helps stakeholders focus on areas most relevant to their responsibilities.
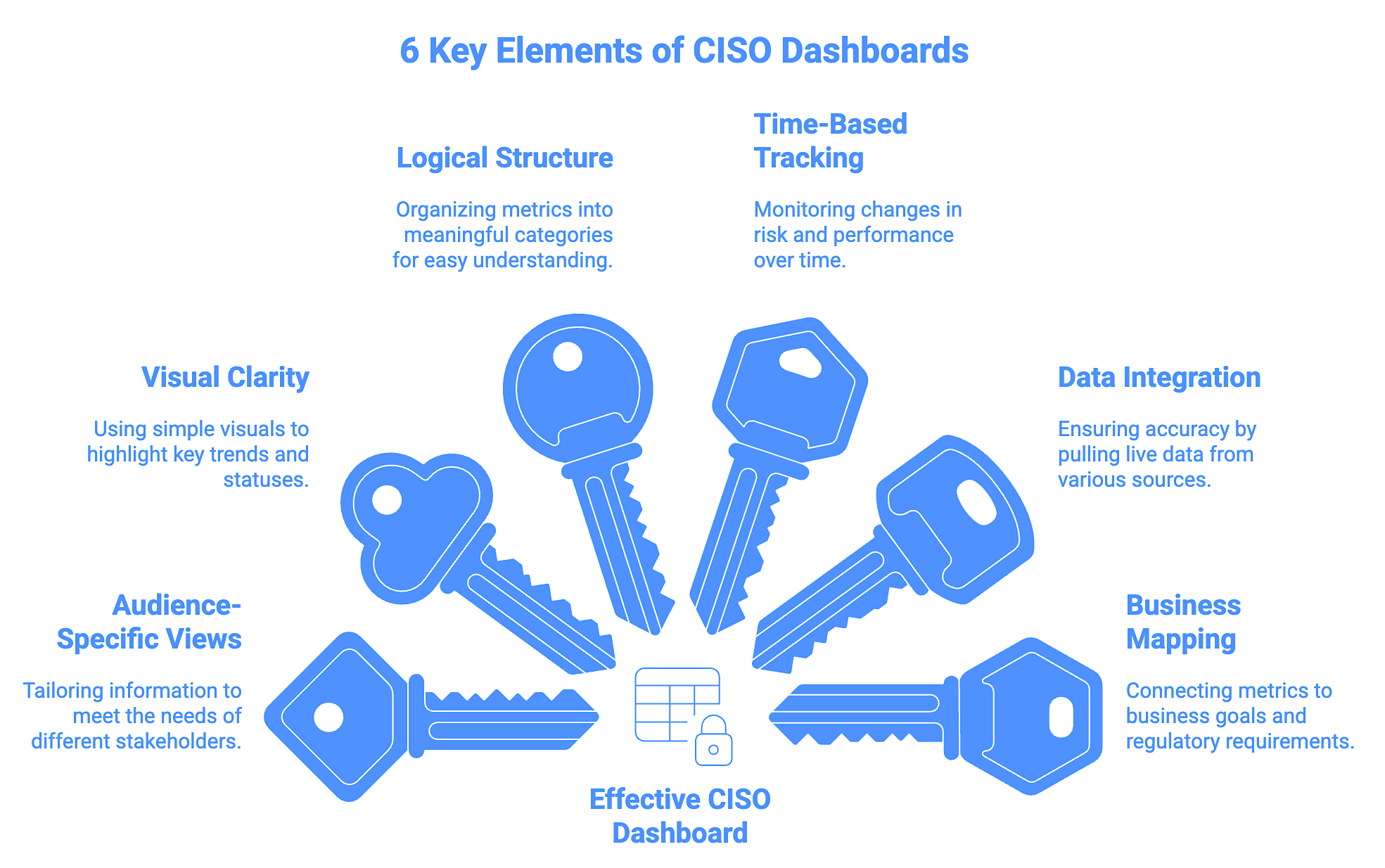
4. Time-based Tracking
Dashboards should present how risk and performance change over weeks, quarters, or years to show whether cybersecurity investments are making a measurable difference.
5. Data Integration
Accuracy depends on pulling live information from Security Information and Event Management (SIEM) tools, Governance, Risk, and Compliance (GRC) tools, vulnerability scanners, and other platforms. Automating these feeds reduces the risk of stale data or inconsistent reporting.
6. Business Mapping
Every metric should connect back to a business goal or regulatory requirement. For example, vulnerability closure rates can be tied to audit readiness, while incident response times can be linked to operational resilience.
What metrics should be included on your CISO dashboard?
Your CISO dashboard should include these metrics that give leaders confidence in the organization’s security posture and demonstrate whether the program is delivering results:
Risk Management
Open risks, aging vulnerabilities, and remediation timelines show where exposure exists and whether risk is being reduced. For added context, CISOs often include risk ownership and the proportion of risks accepted vs. mitigated.
Incident Response
Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) are standard metrics, but dashboards should also track incident volumes over time and containment rates. These indicators show how quickly teams react—and whether they are closing the loop effectively.
Vulnerability Management
Time to patch, severity-weighted vulnerability counts, and the backlog of unresolved findings highlight the organization’s ability to manage known threats. A trendline on time-to-remediate for critical vulnerabilities adds important visibility for executives.
Compliance Status
Boards and regulators want assurance that frameworks such as NIST, CMMC, ISO 27001, and SOC 2 are being met. Dashboards should reflect alignment status, open audit gaps, recurring non-conformities, and upcoming assessment milestones.
Third-party Risk
Vendors are a growing source of exposure. Dashboards should display supplier classifications, outstanding risk assessments, and unresolved findings. Tracking the number of critical suppliers without a current assessment provides boards with a clear view of supply chain gaps.

Security Awareness
Completion rates for training programs and phishing simulation results remain foundational, but dashboards should also highlight repeat offenders or trends in user-reported phishing. These metrics provide a fuller picture of organizational resilience.
Access Governance
Inactive privileged accounts and overdue access reviews should always be monitored. Some organizations also track the ratio of standing to just-in-time privileged access as a way to measure maturity.
Cloud Security Posture
Metrics such as misconfigurations, untagged assets, and over-permissioned roles are essential in cloud-heavy environments. Including exposure to known critical misconfigurations (for example, open storage buckets) provides executives with an immediate understanding of risk.
Defense and DoD-specific indicators
For organizations supporting defense contracts, metrics such as the Supplier Performance Risk System (SPRS) score and security controls maturity are critical. These demonstrate compliance with NIST 800-171 and CMMC requirements, both of which directly impact eligibility for contracts.
Dashboards that incorporate these metrics alongside broader security and compliance indicators reinforce readiness for regulatory reviews and provide leadership with confidence that obligations tied to defense work are being met.
How to Build a CISO Dashboard: 9 Practical Tips
Tip 1: Know Your Audience
A dashboard must reflect the needs of its audience. Executives want a high-level view of risk in business terms, boards expect evidence of oversight, and operational teams need the detail to manage incidents and remediation. Designing audience-specific views ensures each group gets information in a format they can act on, which makes the dashboard relevant and credible.
How to do it:
- Identify the core audiences for your dashboard: executives, board members, compliance officers, and technical teams.
- Build audience-specific views, such as summary scorecards for leadership and detailed operational metrics for IT and security staff.
- Use role-based access controls to deliver the right level of visibility to each group while protecting sensitive information.
- Revisit audience requirements on a regular basis to ensure dashboard views remain aligned to business and operational priorities.
Tip 2: Define Clear Objectives
Clear objectives ensure that your CISO dashboard tells a coherent story. They align the data displayed with the organization’s strategy, whether that is improving audit readiness, reducing incident response times, or showing progress toward closing vulnerabilities. This focus helps executives and boards see not just activity but outcomes that matter to the business.
How to do it:
- Ask stakeholders what questions they need answered most often by security reporting.
- Narrow the focus to a small set of primary objectives, such as compliance tracking, incident response, or vulnerability management.
- Prioritize data points that directly address those objectives and eliminate metrics that don’t serve a clear purpose.
- Reassess objectives periodically as business priorities and compliance requirements evolve.
Tip 3: Choose Business-Relevant Metrics
Highlight metrics that show the business impact of security efforts, such as reduced exposure to critical risks or audit readiness. Boards and executives need to see evidence that investments are reducing risk and enabling the company to meet regulatory or contractual obligations. Choosing the right metrics ensures the dashboard functions as both a security tool and a resource for decision-making.
How to do it:
- Prioritize key performance indicators (KPIs) that link security outcomes to business objectives, such as risk reduction or cost avoidance.
- Avoid vanity metrics that don’t influence decisions or strategy.
- Engage executives and compliance teams to validate which measures matter most for funding and oversight.
- Ensure metrics can be consistently tracked and updated, so they retain credibility over time.

Tip 4: Prioritize Visual Simplicity
Dashboards are most effective when they make complex information easy to understand at a glance. Executives and boards often only have a few minutes to review security updates, and a cluttered or overly technical dashboard slows them down. Simple formats like scorecards, traffic-light indicators, and trend arrows allow users to quickly see where the organization is improving, where risks remain, and where resources may be needed.
How to do it:
- Limit each view to a handful of high-value metrics.
- Use consistent colors, labeling, and chart styles across all dashboard views.
- Favor clean visuals such as line trends, scorecards, or risk heat maps over dense or complex charts.
- Test dashboard views with stakeholders to ensure the message is immediately clear without additional explanation.
Tip 5: Ensure Data Accuracy & Integrity
Dashboards built on well-governed and accurate data become a trusted source of truth. They allow CISOs to stand in front of boards and regulators with confidence, knowing the numbers reflect the organization’s real security posture. That trust is critical when making the case for budgets, demonstrating compliance, or responding to incidents.
How to do it:
- Automate data ingestion from systems such as SIEMs, vulnerability scanners, and compliance tools to reduce manual errors.
- Standardize definitions for each metric so all stakeholders interpret them the same way.
- Assign ownership for data sources to ensure accountability and ongoing validation.
- Establish processes for regular quality checks and ensure timestamps are visible so audiences know data is current.
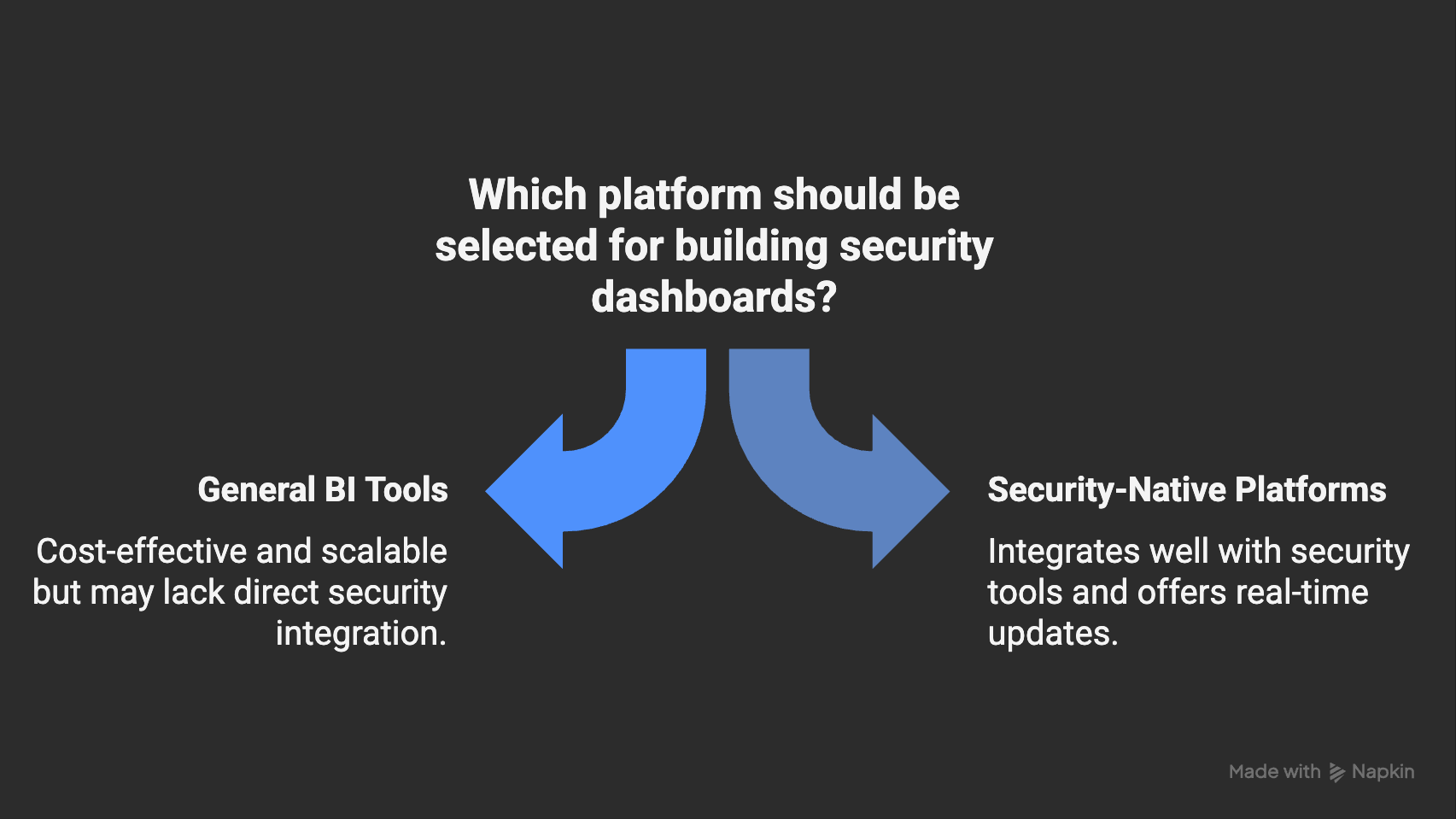
Tip 6: Select the Right Platform
The platform you build your CISO dashboard on determines how effective it will be. Some organizations lean on general business intelligence tools, while others prefer security-specific platforms that integrate directly with your existing tools. A good fit allows CISOs to pull data from multiple systems into a single trusted view, present metrics in executive-friendly formats, and update dashboards in real-time. It also makes the dashboard easier to sustain as your security program evolves.
How to do it:
- Compare general-purpose BI tools and security-native dashboards based on cost, scalability, and integration capabilities.
- Prioritize platforms that connect easily to your core tools, such as SIEMs, IAM systems, vulnerability scanners, and compliance software.
- Involve both technical teams and executives in platform evaluation to ensure the final product meets diverse needs.
- For organizations with a mature vCISO program, coordinate platform selection across security, IT, and business leadership to align metrics with both risk and strategy.
Tip 7: Integrate Data from Security Tools
A CISO dashboard becomes truly valuable when it brings together information from across the security stack and updates it automatically. Integrating data directly from tools ensures accuracy and timeliness. When feeds from your security systems flow into a single view, leaders gain a complete picture of the organization’s security posture. These integrations save time, reduce human error, and provide confidence in the numbers presented.
How to do it:
- Use secure APIs or ETL (Extract, Transform, Load) processes to connect key platforms directly into the dashboard.
- Standardize data formats across tools to make integration smoother and reporting more consistent.
- Automate updates so dashboards refresh in near-real time without requiring manual effort.
- Test the data pipeline regularly to confirm feeds remain accurate and secure.
Tip 8: Iterate & Refine Based on Feedback
A CISO dashboard should adapt to changing risk environments, compliance requirements, and executive priorities. Treating the dashboard as a continuously evolving tool ensures it stays aligned with both business strategy and security realities. Regular refinement also builds trust with stakeholders. When executives see that their feedback is incorporated, they are more likely to engage with the dashboard consistently.
How to do it:
- Schedule regular reviews with executives, compliance officers, and technical teams to capture feedback.
- Adjust visuals for clarity and retire metrics that are not being used in decision-making.
- Add new metrics when regulatory changes, emerging risks, or business priorities require additional visibility.
- Document any changes over time so stakeholders can see the evolution of reporting alongside the evolution of the program.
Tip 9: Make the Dashboard Part of Regular Executive Rhythm
For maximum effectiveness, the CISO dashboard needs to be part of the organization’s governance rhythm by showing up in the meetings and reports that shape decisions.
Over time, the dashboard becomes the common reference point for measuring progress and aligning security with business strategy.
How to do it:
- Present key dashboard views during monthly leadership meetings and quarterly board reviews.
- Incorporate dashboard outputs into audit preparation and compliance reporting cycles.
- Share concise, executive-friendly extracts alongside financial and operational reporting to emphasize alignment.
- Encourage leaders to reference the dashboard as the authoritative source when discussing security performance.
Turn Your CISO Dashboard into a Strategic Tool
A well-designed CISO dashboard creates a shared language between technical teams and executive leaders. It shows whether security investments are reducing vulnerabilities, response processes are improving, and compliance obligations are met. When integrated into executive decision-making, dashboards become strategic tools that align cybersecurity with business objectives and strengthen accountability across the organization.
Custom CISO dashboards are a core component of Vistrada’s vCISO services. We design, build, and maintain executive-ready Apptega dashboards, integrate the right data sources, and embed them into monthly and quarterly leadership reviews so decision-makers can act with confidence.
With vCISO services, clients receive cybersecurity leadership supported by CIO and CTO perspectives and a bench of specialists who execute across assessments, policy development, training, and incident response. This team-based model pairs visibility with hands-on execution, turning dashboard reporting into measurable progress.
Connect with Vistrada to explore how our vCISO service goes beyond dashboards to deliver meaningful cybersecurity program improvements.




