Fortune 500 companies have placed a growing emphasis on cybersecurity in recent years. However, with the growing penetration of advanced AI technologies, mid-market businesses are under growing pressure to meet security and compliance demands as well. While risks escalate, budgets shrink, and talent remains scarce. But recruiting top cybersecurity talent is not only difficult, it’s also expensive.
By 2025, the median annual compensation for a Chief Information Security Officer (CISO) reached $532,000, and the top 10% of CISOs reported earning more than $1.3 million per year. Even with these salaries, the risk of burnout in this role is real. 70% of CISOs say personal liability and stress have soured their view of the role. Faced with growing costs, a lack of experienced personnel, and high turnover rates, many mid-market organizations are embracing the virtual CISO (vCISO) model.
A vCISO provides executive-level cybersecurity leadership on a flexible basis, typically costing 30–70% less than a full-time hire. A vCISO goes beyond fractional CISOs or Managed Security Service Providers (MSSPs) by also covering assessments, training, compliance readiness, and board reporting on demand.
The question is, how do you hire the right vCISO partner to guide your organization through today’s cybersecurity and compliance challenges? Let’s explore what vCISOs do, how to tell if the role is a good fit for your organization, and the steps to engaging the right one.
What is a vCISO, and what do they do?
One of the most common types of CISO-as-a-Service (CaaS), a virtual Chief Information Security Officer (vCISO) delivers ongoing, outsourced executive-level cybersecurity leadership, strategy, oversight, and execution on a subscription basis. Unlike a fractional CISO who may show up quarterly, or a consultant who provides advice but no follow-through, a vCISO service can offer a lot more than a single CISO can.
The vCISO model is designed to fill the gaps most mid-market organizations face in securing their digital assets and maintaining compliance:
- Small IT teams may be strong on day-to-day operations, but rarely have the capacity or expertise to meet complex compliance and reporting needs.
- Managed service providers (MSPs) can keep systems running but are not equipped to deliver leadership, policy, risk management, or board-level reporting.
This is where a virtual CISO steps in to provide the direction and accountability that smaller IT teams and MSPs cannot offer.

Ideally, vCISO services are structured for availability, scalability, and access to a breadth of expertise. In practice, this means you get to leverage the knowledge of a seasoned CISO, and also that of a variety of specialists who can execute risk assessments, develop and implement policies, conduct training, and respond quickly to incidents.
Key Responsibilities of a Virtual CISO (vCISO)
The typical responsibilities of a vCISO encompass both the vision of an executive leader and the hands-on support needed to develop and execute cybersecurity programs. These include:
- Security risk assessments – Identifying security vulnerabilities and prioritizing their remediation.
- Framework alignment – Mapping security controls to industry frameworks like CMMC 2.0, NIST, SOC 2, ISO 27001, PCI-DSS, and other standards.
- Policy development and enforcement – Creating and maintaining security policies aligned with business needs.
- Incident response planning – Creating and testing playbooks with tabletop exercises.
- Vendor and supply chain risk management (C-SCRM) – Evaluation of third parties and protection of sensitive data across partners and channels.
- Cybersecurity awareness training – Conducting training programs and running phishing simulation campaigns to reduce human risk.
- Vulnerability scanning and insurance review – Testing defenses regularly and ensuring cyber insurance requirements are met.
- Executive and board reporting - Translating technical issues into business language for leadership and stakeholders.
- Compliance support - Preparing for audits, managing evidence, and filling out customer and regulator questionnaires.
- Technology and GRC integration - Employing dashboards and reporting tools to track progress and compliance in real time.
Unlike a one-time consultant, a virtual CISO ensures these responsibilities are carried out continuously, embedding cybersecurity leadership into day-to-day operations.
Why Hire a vCISO?
Can your business benefit from hiring a vCISO? Organizations typically hire a vCISO to:
- Alleviate compliance and audit pressures by delivering expert guidance on regulatory requirements and customer demands without delaying business processes.
- Manage cybersecurity investments effectively with access to leadership at a predictable rate that is a fraction of the six-figure salary of a full-time CISO.
- Lead strategy and execution, with the vCISO continuously engaged with the organization to provide training, development of up-to-date policies, and incident response plans.
- Align cybersecurity with business priorities to ensure investments directly support revenue, resilience, growth, and customer trust.
- Tap into a wealth of expertise with vCISO services that give you access to skills across risk management, cloud, governance, supply chain, and incident response that no single hire can cover.
- Enhance partner and customer trust by demonstrating security maturity and standard compliance as a competitive differentiator in bids and renewals.
- Strengthen competitiveness in regulated industries by meeting compliance requirements that are often mandatory for securing and retaining contracts.
If these challenges resonate with your organization, engaging a vCISO can provide the leadership and execution needed to protect your business and position it for growth.
- Detection and Identification of Incidents: The initial phase in incident response is the detection and identification of potential threats. This process requires continuous monitoring of network traffic and system activities, utilizing advanced tools like intrusion detection systems (IDS) and security information and event management (SIEM) systems. Effective detection hinges on the ability to distinguish between normal and anomalous activities, requiring skilled personnel who can interpret alerts and decide on the appropriate course of action.
- Containment Strategies and Techniques: Once an incident is detected, immediate containment is essential to prevent further damage. This involves isolating affected systems, potentially disconnecting them from the network, and implementing short-term fixes. Containment strategies should be tailored to the type of incident, whether it’s a network breach, malware infection, or an insider threat. Effective containment minimizes the impact on business operations and buys time for a more comprehensive response.
- Eradication and Recovery Measures: Eradication involves removing the threat from the organization’s systems, which may include deleting malicious files, closing security loopholes, or updating compromised credentials. Following eradication, the recovery process begins, aiming to restore affected systems and data to their pre-incident state. This phase also involves implementing measures to prevent similar incidents in the future, informed by the insights gained during the incident.
- Post-Incident Analysis and Reporting: Post-incident analysis is critical for understanding how the incident occurred, assessing the effectiveness of the response, and identifying areas for improvement. This analysis should be thorough, involving a review of how the incident was detected, the steps taken to respond, and the processes used for recovery. Detailed reporting helps in documenting the incident for future reference and compliance purposes.

How to Hire the Right vCISO: A Step-by-Step Guide
To streamline your virtual CISO hiring process, follow this detailed, seven-step guide:
Step 1: Define Drivers, Scope, and Success Criteria
Begin the virtual CISO hiring process by answering four key questions:
1. Why now?
First, name the hiring trigger, such as an upcoming audit, enterprise customer requirement, security incident, M&A, or insurance renewal. Detail the potential risk to your business if no steps are taken to remedy the situation. This framing helps show not just the security risk, but also whether inaction could delay contracts or compliance milestones that matter to the business.
2. What’s in scope?
Next, identify the business units, systems, and data classes in play, as well as any specific obligations, such as applicable frameworks or contractual requirements, due in the near future (6-12 months).
3. What is expected?
Then, manage expectations by setting measurable goals and expected results, like passing an audit by a specific date, closing the top 10 riskiest vulnerabilities in your systems, or achieving industry-specific framework compliance.
4. Who’s accountable?
Finally, list all the stakeholders and decision-makers across the answers to the previous three questions, as well as the cadence of collaboration your organization follows, such as weekly working sessions and periodic board updates.
With this information in hand, you can create a deliverable to hand to your virtual CISO candidate that will help them right-size your plan rather than offer a generic package. You may also want to share a rough systems and applications inventory and any past audit findings.
Step 2: Confirm Industry and Framework Expertise
Not all vCISOs offer the same services. For example, a provider who knows financial services won’t necessarily understand defense contracting or healthcare compliance.
Before you engage, confirm that the candidate has direct experience in your industry’s regulations, contracts, best practices, and unique risks. Ask for case studies or anonymized audit prep materials to ensure the vCISO isn’t learning your industry at your expense.
Key areas to check include:
- Framework expertise – Have they guided clients through the certification process of frameworks that are relevant to your industry and business? Can they provide examples of successful audits or certifications?
- Sector-specific risks – Are they proficient with issues relevant to your industry, like controlled unclassified information (CUI) in defense, payment card data in retail, or patient privacy in healthcare?
- Expectation alignment – Can they demonstrate how they’ve helped similar companies achieve their compliance goals?
For many mid-market organizations, this expertise isn’t available in-house. That makes it essential to validate that a vCISO can bring proven experience in your industry to the table on day one.
Step 3: Evaluate the Service Model
Similarly, not all virtual CISO service providers define the role in the same way. Some offer little more than a fractional executive who serves as an advisor on a quarterly basis. Others provide a solo consultant who can help develop policies, but lacks the bandwidth for deeper execution.
For mid-market businesses, the most effective virtual CISO approach is team-based, which usually means there’s a lead CISO with a range of specialists for specific needs. This setup equips your organization with a CISO for strategic direction, who is supported by experienced pros that handle risk assessments, training, vendor reviews, and GRC onboarding.
A team-based model gives mid-market organizations both breadth and continuity of expertise. It also delivers these benefits at a lower cost than building an in-house team or relying on a single fractional consultant.
When comparing vCISO provider services and their models, consider:
- Will you be working with a single person or a team?
- How often will they engage? Ad-hoc only? Periodically? Is that enough time to meet your needs?
- What capabilities can the vCISO service provider offer beyond advisory services alone?
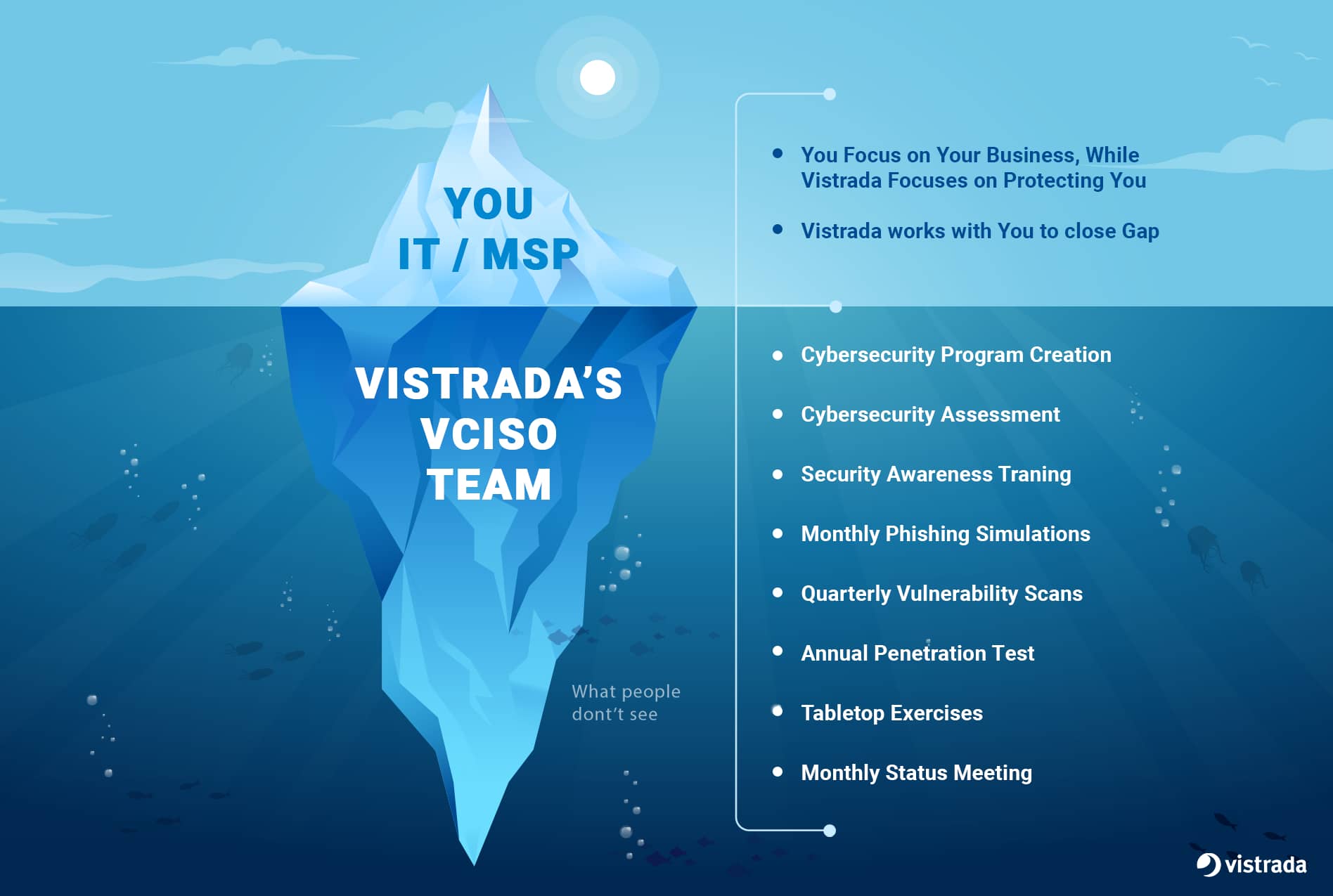
Step 4: Understand the Scope of Strategy and Execution
A vCISO engagement should be more than a checklist or a slide deck. Instead, a strong vCISO relationship begins with a clear definition of what they will do for your business. Too often, organizations assume execution is included in the deal, only to discover later that they’ve paid for advice without hands-on support.
To avoid this gap, make sure to ask candidates to outline the full cycle of their typical engagement. Clarify how often they will engage with your team, since a quarterly check-in is rarely enough to drive progress in a mid-market environment.
Check if the vCISO services provide:
- Strategic planning and risk prioritization.
- Implementation support, like developing policies or running incident response exercises.
- Ongoing oversight, including progress tracking and executive reporting.
Look for concrete examples of deliverables. A mature vCISO service should provide you with actionable documents and a measurable improvement in your security posture.
Step 5: Compare Pricing Models
vCISO engagement pricing will tell you more about the provider than just how much you will be investing. It will show you how flexible the vCISO you hire will be, and how the service can scale up or down with your business needs. For many mid-market organizations, predictable monthly pricing can be as important as the breadth of services provided.
Common vCISO pricing structures include:
- Retainer-based with a predictable monthly cost that covers a defined set of services and work hours.
- Tiered packages that offer different levels of support according to specific needs, such as compliance readiness, or a premium level that includes board reporting and more.
- Project-based pricing is best for scoped engagements tied to a specific deliverable, like a certification audit checklist.
When comparing providers, focus on return on investment. Low-cost packages may provide templates but lack support, while higher-priced retainers often include training, vendor reviews, and incident readiness that improves your security posture.
Step 6: Ask for References
Polished proposals can’t show you how a vCISO performs in practice. This is why it is essential to speak directly with past or current clients, and review real examples of the virtual CISOs past work. When speaking to references, focus first on key areas that matter to you, then review the following factors.
Virtual CISO factors to prioritize:
- Responsiveness – How quickly did the hired vCISO step in when an urgent request came in or a cybersecurity incident occurred?
- Collaboration – Did the vCISO work seamlessly with IT staff, MSPs, business units, and leadership?
- Results – What tangible values has the vCISO brought to the business? Did they help close audit findings, or secure new contracts through standard compliance certification? Also, ask whether the vCISO consistently delivered over the course of the engagement, since sustained performance is as important as individual results.
Step 7: Align on Collaboration
A virtual CISO should feel like a seamless extension of your leadership team, so expectations must be clear before the deal is signed. Ensure both sides agree on roles, responsibilities, and communication cadence before the engagement begins. For example, mid-market organizations often benefit from a monthly cadence, which keeps progress moving without the gaps common in quarterly check-ins.
Key areas of collaboration to consider:
- Frequency of interaction – Will you meet weekly, monthly, or only for specific milestones? What happens in between?
- Reporting style – Will you receive detailed technical updates or concise executive summaries for leadership and the board, or both?
- Tooling – Will the vCISO service provider plug into your existing ticketing, GRC, or collaboration tools, or introduce their own dashboards?
- Escalation paths – Who do you call in case of a severe cyber incident, and how quickly should you expect a response?

Vistrada’s vCISO Service: The Best of All Worlds
Hiring a virtual CISO is about securing leadership that can translate cybersecurity into business value. It means ensuring that compliance demands are met, your organization is prepared and ready for incidents, and that there’s a steady, experienced hand guiding both strategy and execution of cybersecurity programs. This leadership also positions organizations to pass audits, improve SPRS scores, and compete more effectively for contracts in regulated industries.
Many vCISO providers offer only a single consultant or fractional resource. Vistrada’s vCISO service goes further. We deliver a team-based model that combines the vision of an experienced CISO with specialists who handle assessments, policies, training, incident response, and GRC onboarding. Clients also gain CIO and CTO perspectives, with a regular monthly cadence that ensures progress is monitored regularly. The outcome is sustained cybersecurity leadership with measurable improvements in resilience and compliance readiness.
Contact Vistrada today to discover how our team-based vCISO services can strengthen your cybersecurity program and give your business a competitive edge.




