Where cyber threats loom large, the significance of robust cybersecurity measures is paramount. An Incident Response Policy is not just a set of guidelines; it’s a critical defense mechanism for any organization. This policy is an organization’s first line of defense, a carefully crafted response plan to manage and mitigate the impacts of cybersecurity threats. It involves identifying, managing, recording, and analyzing cybersecurity events or incidents for containment and eradication, and to ensure the appropriate response and recovery for business as usual.
Foundations of Incident Response
An Incident Response Policy is a systematic approach to handling and managing the aftermath of a security breach or cyberattack. It is a framework that provides the necessary steps for detecting, investigating, and responding to cybersecurity incidents. The policy is designed to help organizations respond swiftly and effectively, minimizing damage and reducing recovery time and costs. It also includes procedures for reporting incidents to relevant authorities and stakeholders.
Initially, incident response was a reactive measure, but it has evolved into a proactive strategy. This evolution reflects the growing complexity and frequency of cyber threats. Modern policies are comprehensive, integrating technology, people, and processes to address the dynamic nature of cybersecurity risks.
Designing an Incident Response Policy
An effective Incident Response Policy is characterized by several key elements. It must offer clear guidance on the initial response, outline the steps for containment and eradication, and provide protocols for recovery and post-incident analysis. Equally important is the establishment of a command structure and clear lines of communication, ensuring that all team members know their roles and responsibilities and can act swiftly and decisively.
The success of an incident response hinges on the coordinated efforts of various stakeholders. This includes not only the IT and cybersecurity teams but also extends to legal, HR, public relations, and executive management. Each group plays a critical role, from managing technical aspects to handling legal repercussions and communicating with external stakeholders. This collaborative approach is fundamental to an effective incident response.
Effective incident response often requires collaboration with external agencies. This collaboration can range from engaging cybersecurity firms for their technical expertise to working with law enforcement for legal compliance and investigation. Establishing relationships with these external entities before an incident occurs can streamline the response process. The policy should outline when and how to engage these agencies, ensuring that their involvement is timely and coordinated with the internal response team’s efforts.
For a seamless and expertly coordinated incident response, partnering with a seasoned cybersecurity firm like Vistrada can make all the difference. Vistrada specializes in providing comprehensive cybersecurity solutions, ensuring your organization is prepared and resilient against cyber threats.
If you’re seeking to enhance your incident response capabilities and establish effective collaborations for your cybersecurity needs, contact Vistrada today.
The Incident Response Process
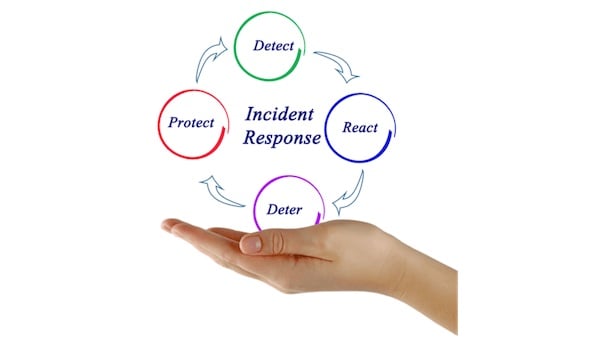
- Detection and Identification of Incidents: The initial phase in incident response is the detection and identification of potential threats. This process requires continuous monitoring of network traffic and system activities, utilizing advanced tools like intrusion detection systems (IDS) and security information and event management (SIEM) systems. Effective detection hinges on the ability to distinguish between normal and anomalous activities, requiring skilled personnel who can interpret alerts and decide on the appropriate course of action.
- Containment Strategies and Techniques: Once an incident is detected, immediate containment is essential to prevent further damage. This involves isolating affected systems, potentially disconnecting them from the network, and implementing short-term fixes. Containment strategies should be tailored to the type of incident, whether it’s a network breach, malware infection, or an insider threat. Effective containment minimizes the impact on business operations and buys time for a more comprehensive response.
- Eradication and Recovery Measures: Eradication involves removing the threat from the organization’s systems, which may include deleting malicious files, closing security loopholes, or updating compromised credentials. Following eradication, the recovery process begins, aiming to restore affected systems and data to their pre-incident state. This phase also involves implementing measures to prevent similar incidents in the future, informed by the insights gained during the incident.
- Post-Incident Analysis and Reporting: Post-incident analysis is critical for understanding how the incident occurred, assessing the effectiveness of the response, and identifying areas for improvement. This analysis should be thorough, involving a review of how the incident was detected, the steps taken to respond, and the processes used for recovery. Detailed reporting helps in documenting the incident for future reference and compliance purposes.
Incident Response Training and Tools
A competent incident response team is essential for effective cybersecurity management. This team should consist of individuals with diverse skills, including technical expertise in various areas of cybersecurity, as well as skills in communication and problem-solving. Regular training and professional development are crucial to keep the team updated with the latest threats and response techniques.
Conducting regular training sessions and drills is vital to ensure that the incident response team and the broader staff are prepared to handle potential cybersecurity incidents. These exercises should simulate a range of scenarios, from common threats like phishing to complex, multi-faceted attacks. Regular drills help in identifying gaps in the response plan and provide opportunities for improvement.
The effectiveness of an incident response depends heavily on the tools and technologies employed. Essential software includes IDS, SIEM systems, antivirus programs, and forensic tools. On the hardware front, secure servers, firewalls, and backup systems are crucial. Investing in quality software and hardware is fundamental to a robust cybersecurity posture.
The integration of AI and Machine Learning in incident response is revolutionizing how organizations handle cybersecurity threats. These technologies offer advanced capabilities for predictive analytics, automated detection, and rapid response to incidents. AI algorithms can analyze vast data sets to identify unusual patterns indicative of a security breach, enabling organizations to preemptively address vulnerabilities. Machine Learning enhances this process by continuously learning from data inputs, improving threat detection over time. The use of AI and ML in incident response not only accelerates the identification and containment of threats but also significantly improves the accuracy and efficiency of the overall cybersecurity strategy.
While AI and ML can significantly enhance incident response, they also introduce their own set of unique challenges. To gain a nuanced understanding of these challenges and how they impact data security, we invite you to explore our eBook, ‘Data Security Challenges in the AI Era.’
FAQs
- What is an Incident Response Policy? An Incident Response Policy is a structured plan that outlines the procedures an organization should follow in the event of a cybersecurity incident. It includes guidelines for detection, response, containment, eradication, and recovery from cyber threats.
- How Often Should Incident Response Policies be Reviewed? Incident Response Policies should be reviewed and updated regularly, at least annually, or in response to significant changes in technology, threat landscapes, or business operations. This ensures that the policy remains relevant and effective against current cyber threats.
- What are the Legal Implications of an Ineffective Incident Response Policy? An ineffective Incident Response Policy can lead to severe legal consequences, including regulatory fines, legal action, and damage to reputation. Non-compliance with industry standards and privacy laws can result in significant liabilities for organizations.
- How Can You Ensure All Employees Understand the Incident Response Policy? Ensuring all employees understand the Incident Response Policy involves regular training sessions, clear communication of procedures, and engaging training materials. Simulated cyberattack exercises can also help employees understand their roles and responsibilities during an incident. Regular updates and refreshers are necessary to keep the knowledge current and top of mind.




